Accessing my Pi When I’m on the Go
I travel a good bit (or at least used to). I’d like to be able to admin my home network wherever I am. This is a little tough because I don’t have a static IP address at my apartment. At any point the external address of my router relative to the internet could change.
One option available to me is to use something like DYN DNS. DYN DNS allows for your network to dynamically configure it’s DNS address. The issue is that Dyn DNS is $55 a year, which is like a ¼ of a Pinebook.
Cryptography to the Rescue
One approach to providing a way to route to my server without having an static IP is to use one of the volunteer run cryptographic overlay networks.
Here are two,
When exposing a server to inbound connections via something like Tor, all connections from your server are outgoing to the Tor network. This means that you can make a server routable on any network that can reach the Tor network.
Overlay networks like I2P and Tor use cryptographic signatures to route within the network. Addresses look like http://bbcnewsv2vjtpsuy.onion. Addresses look weird because they’re the public keys (or just the hash in the case of the old ones) of the servers. Since routing is done with cryptographically, you don’t need something like a lease on the limited IPv4 address space.
On my Pi (I’ve named it io after Jupiter’s moon) I can expose the ssh server via Tor by using the following configuration. We tell the Tor process to forward incoming connections on port 22 to port 22 on the loopback (localhost)
After installing tor (apt install tor), I added this to my /etc/tor/torrc file
RunAsDaemon 1
DataDirectory /var/lib/tor
HiddenServiceDir /var/lib/tor/ssh_hs/
HiddenServicePort 22 127.0.0.1:22
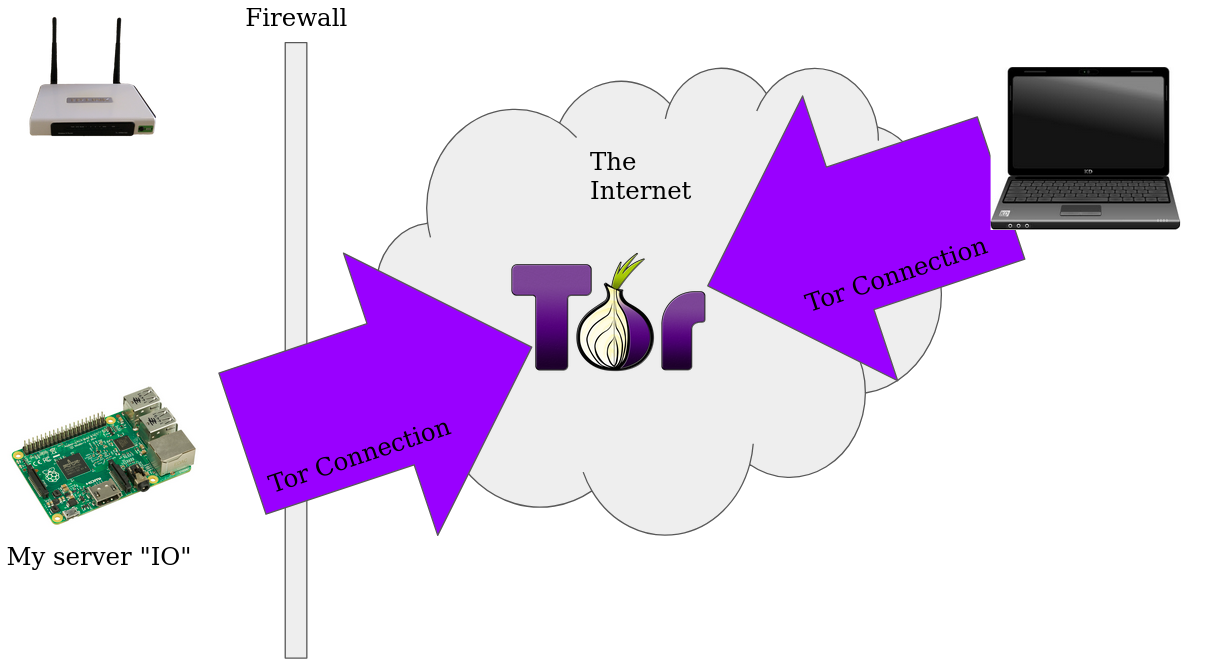
Connecting my Laptop to Tor
There’s a special version of Firefox that ships configured with all the necessary software to connect to the Tor network. When you run the Tor browser, it also runs a SOCKS5 proxy on port 9150 that any other software can use.
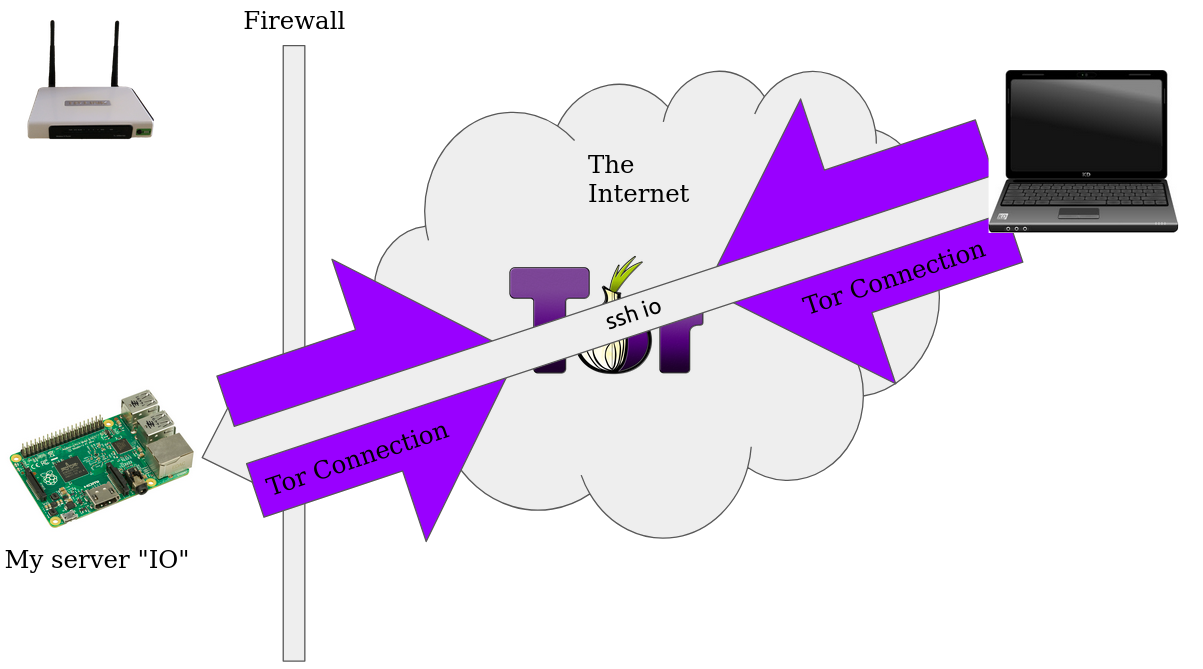
On my laptop I can tell ssh to proxy commands through the Socks5 Proxy by editing my ~/.ssh/config like so
Host io
Hostname <your-onion-address>.onion
User pi
IdentityFile ~/.ssh/id_rsa
ProxyCommand nc -X 5 -x localhost:9150 %h %p
VerifyHostKeyDNS no
CheckHostIP no
IdentitiesOnly yes
Note: I found out the hard way, currently only the BSD edition of netcat supports SOCKS5, and the GNU version does not
Most commands that deal with connecting to a server read the ~/ssh/config file. So ssh and scp work out of the box.
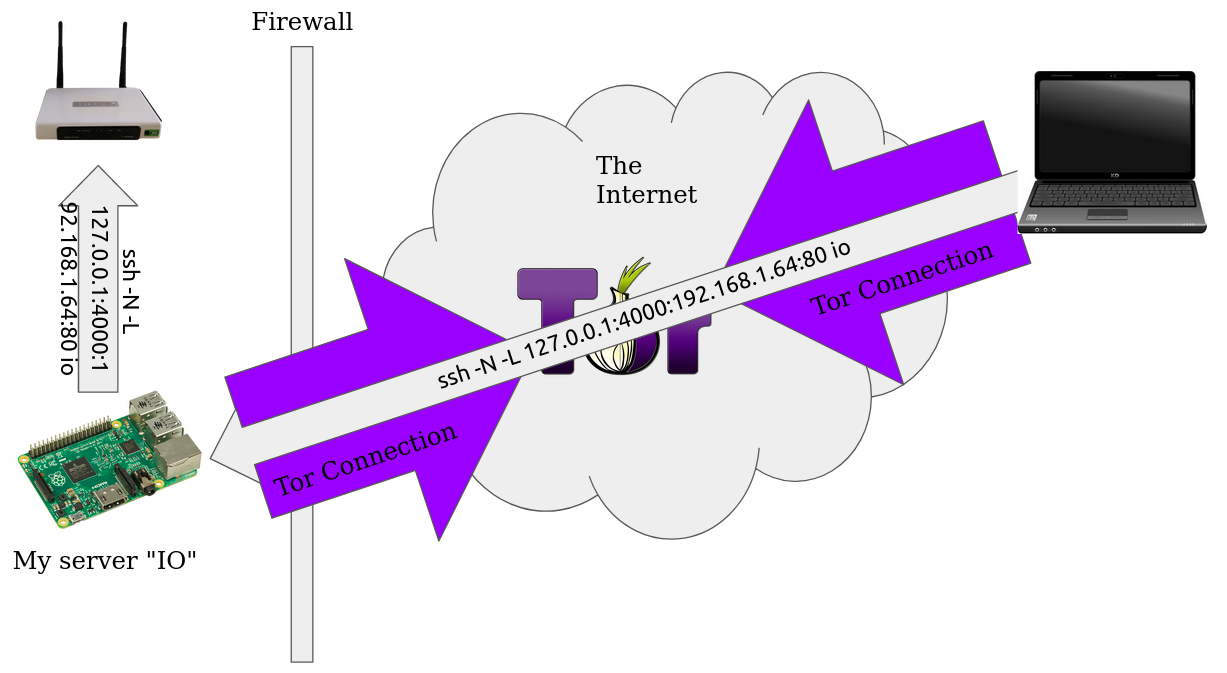
Tunneling
One of my big use cases for is being able to fix the our router for my roomates when I’m on the go. Now that we have a way to do ssh connections over Tor, we can use ssh to tunnel to other places behind my firewall.
ssh -N -L 127.0.0.1:4000:192.168.1.64:80 io
This will forward all connections to port 4000 on your local machines through Io to port 80 on 192.168.1.64 (relative to Io). This means I can use chrome to access my router anywhere I go.